Penetration test, often called “penetration testing or pen testing,” is a simulated cyberattack against your systems to identify security vulnerabilities before real attackers do. The goal is to uncover potential entry points and weak spots that could be exploited to access sensitive data, disrupt operations, or damage reputation. Pen testing is a critical part of modern cybersecurity strategies, as it provides insight into the effectiveness of existing security controls and helps organizations take corrective actions before actual harm is done.
Penetration testing (pen test) is a good mechanism to achieve your goals—whether you need to show compliance with regulations to satisfy a petition from senior management or exhibit security maturity to your clients. The corporate computing environment poses many challenges and security risks such as security incidents, hacks, information theft, denial of service, and more. All of these can severely damage the organization’s current activities and may cause it to lose significant revenue, abandon customers, and suffer reputational harm.
Most organizations are targets for cyber attacks and hacks. To ensure that the protection of the organization’s critical information and assets is adequate, a quality level of penetration testing is essential. Penetration testing is the practice of examining computer systems, corporate networks, and Internet applications to identify vulnerabilities that attackers can exploit. The information assets located in a company’s network should be tested on a regular basis using real and realistic scenarios that mimic the actions of both external and internal attackers.
The number of entry points to corporate networks is always increasing due to the widespread use of emerging technologies. Therefore, those who aim to damage, duplicate, disrupt, or destroy the organization’s sensitive information will usually look for the easiest and most convenient method—the open loophole in the IT network, the most vulnerable, weak, and hackable area. Our Pen testers team expert’s will check and rate the vulnerabilities, so at the end of the process The organization will be able to plan a strategy and implement it according to its risk and budget.
Our Pen testers team expert’s will check and rate the vulnerabilities, so at the end of the process The organization will be able to plan a strategy and implement it according to its risk and budget.
Why is Penetration Testing Important?
Penetration testing is important because it helps organizations find and fix security gaps before real attackers exploit them. In today’s digital world, cyber threats are everywhere—and they’re evolving fast. A single weak spot in your systems could lead to stolen customer data, financial loss, or a serious hit to your brand reputation. Pen testing gives you a chance to see your network from a hacker’s point of view and understand how easy (or hard) it is to break in.
It’s not just about preventing attacks—it’s also about building trust. Clients, partners, and regulators want to know that your business takes security seriously. By regularly testing your defenses and fixing what’s broken, you show that you’re committed to protecting sensitive data. For many companies, penetration testing is also a must-have to meet compliance standards like GDPR, HIPAA, PCI-DSS, and ISO 27001.
In short: pen testing helps reduce risk, improve resilience, and prove that you’re serious about cybersecurity.
CONTACT US
90% of the businesses who gets hacked
will never be able to recover
Dont Be Next!
GET A QUOTE
PENETRATION TESTING SERVICES
Penetration testing provides far more than a technical checklist — it’s a strategic tool for reducing business risk, ensuring compliance, and strengthening customer trust. Below are the key benefits explained in more detail:
- Proactive Risk Reduction: Instead of waiting for a cyberattack to happen, penetration testing allows you to simulate real-world attack scenarios in a controlled environment. This proactive approach helps identify unknown vulnerabilities, misconfigurations, and logic flaws in applications, networks, or infrastructure. Fixing these weak spots before a real attacker finds them can prevent data breaches, service disruptions, or financial loss.
- Regulatory and Industry Compliance: Many global security standards and regulations require regular testing of IT systems. For example, GDPR, HIPAA, PCI-DSS, and ISO/IEC 27001 all include guidelines for ongoing security assessments. A well-documented pen test report helps demonstrate compliance during audits and avoids penalties. It also shows regulators and clients that your organization takes its legal and ethical responsibilities seriously.
- Improved Security Awareness and Team Readiness: Pen testing doesn’t just test technology — it tests your people and processes. It evaluates how well your internal teams detect, respond to, and recover from simulated attacks. This creates a valuable opportunity to train your security team, improve your incident response plan, and build a stronger security culture across the organization.
- Enhanced Decision-Making for IT Security Investments: A professional penetration test provides you with clear, prioritized findings, based on actual risks. Instead of guessing where to spend your security budget, you can allocate resources based on evidence — focusing on the most critical vulnerabilities first. This helps justify security investments to management and ensures maximum ROI.
- Stronger Trust and Reputation: In today’s competitive digital environment, your reputation is one of your most valuable assets. Customers, partners, and investors want to know that their data is safe. Sharing the fact that you conduct regular penetration tests — even without revealing technical details — signals that you prioritize cybersecurity. This builds confidence and can become a differentiator in the market.
- Support for Business Continuity: Cyberattacks can bring your business to a standstill. Penetration testing helps identify potential threats that could impact your operational continuity — such as ransomware entry points or vulnerabilities in remote access systems. Addressing these issues in advance keeps your services running smoothly, even under pressure.
Penetration testing is more than just finding technical flaws—it’s a strategic tool that helps organizations truly understand how secure (or vulnerable) they are in the face of real-world cyber threats. The primary purpose is to evaluate the overall security posture of systems, networks, and applications, but its true value goes beyond the scan results.
- Simulating Real-World Attack Scenarios: Penetration tests replicate realistic attacks, allowing organizations to see how a hacker might move through their environment. For example, a test might simulate a phishing attack to gain user credentials and then attempt lateral movement within the network to access confidential financial data.
- Testing Attack Chains and Impact: Many successful cyberattacks don’t rely on a single critical flaw. Instead, attackers chain together several low- or medium-severity vulnerabilities to achieve a much larger breach. Penetration testers are trained to think like attackers—combining misconfigurations, poor access control, and weak encryption to demonstrate how small issues can escalate into serious incidents.
- Discovering What Automated Tools Miss: While automated vulnerability scanners are useful, they can’t replace human intuition. Pen testing uncovers logical flaws, business logic vulnerabilities, and real-world attack paths that scanners might not detect. For example, a logic flaw in a payment gateway allowing negative transaction values might go unnoticed in a traditional scan.
- Understanding Business and Operational Risk: Penetration testing isn’t just about identifying what could go wrong—it’s about understanding the consequences if it actually does. Would customer data be exposed? Could operations be shut down? What would the financial, legal, or reputational damage look like? These tests help organizations prioritize their security efforts based on actual risk.
- Testing Detection and Response Capabilities: It’s not enough to prevent attacks—organizations must also detect and respond in real-time. Pen tests often include elements of red teaming to test whether the security team notices suspicious activity, how quickly they respond, and whether they follow the right protocols.
- Delivering Actionable, Real-World Insights: At the end of the test, the organization receives a detailed report—not just a list of technical vulnerabilities, but clear, prioritized recommendations for fixing them. These findings help improve both technical defenses and human behavior (e.g., training users on phishing awareness).
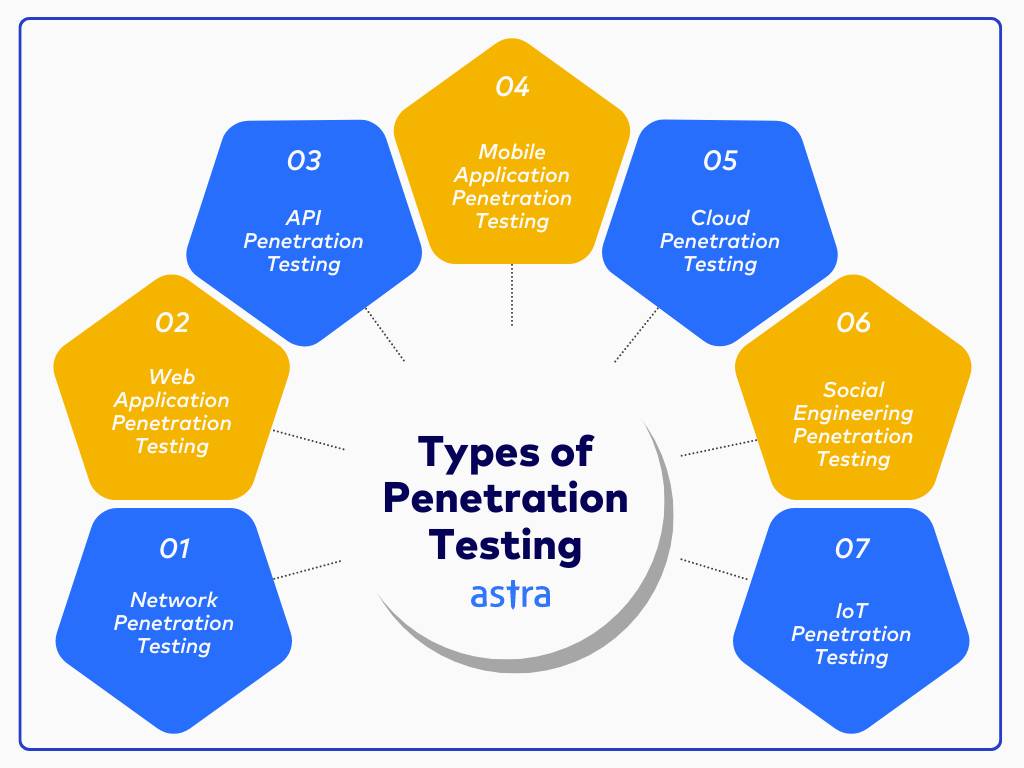
Penetration testing evaluates various components of an organization’s digital and physical environments to uncover vulnerabilities that could be exploited by malicious attackers. Below is a detailed breakdown of the areas commonly tested during a penetration test:
- Network Infrastructure: This includes both internal and external networks—such as routers, switches, firewalls, and servers. Penetration testers simulate attacks to identify issues like open ports, misconfigured services, outdated software, and unauthorized access points. The goal is to determine if an attacker could pivot within the network and escalate privileges.
- Wireless and Local Area Networks (Wi-Fi / LAN): Wireless network testing focuses on the security of your Wi-Fi environment. This includes identifying weak encryption protocols (e.g., WEP, outdated WPA), rogue access points, and opportunities for unauthorized users to intercept or hijack wireless communications. LAN testing evaluates whether internal traffic and device communication are properly secured against threats.
- Web Applications: Web application penetration testing targets vulnerabilities in online systems like customer portals, e-commerce sites, and login forms. Testers look for issues such as SQL injection, Cross-Site Scripting (XSS), broken authentication, and security misconfigurations. This area is often assessed using OWASP Top 10 standards.
- Mobile Applications: Tests on Android and iOS apps identify issues like insecure storage of data, unencrypted transmissions, weak authentication mechanisms, and vulnerable third-party libraries. Both static analysis (of the code) and dynamic analysis (during app execution) are performed to uncover flaws.
- Smart Devices and Embedded Products: This includes testing for vulnerabilities in devices such as printers, IP cameras, smart TVs, and other embedded systems. These products often run proprietary firmware and can be exploited if improperly configured or not regularly updated.
- Cloud Security: Cloud penetration testing involves evaluating configurations, access controls, and deployed services in environments like AWS, Azure, or Google Cloud. Testers check for misconfigured storage (e.g., public S3 buckets), overly permissive IAM roles, exposed APIs, and insecure access points.
- IoT (Internet of Things): Penetration testing for IoT environments focuses on connected devices and their ecosystems. This includes testing firmware, device authentication, communication protocols, and cloud integrations. IoT is particularly vulnerable due to weak security practices during device manufacturing.
- Social Engineering and Physical Security (Optional): In some cases, penetration testing also covers human vulnerabilities—like phishing campaigns or unauthorized access to physical areas. Testers may simulate email scams, phone-based pretexting, or physical entry attempts to evaluate employee awareness and procedural enforcement.
Each of these areas represents a potential entry point for cybercriminals. A thorough penetration test doesn’t just focus on one aspect but rather builds a complete picture of your organization’s security posture, helping you identify and close the gaps before they can be exploited.
Vulnerability assessments are one of the most practical and cost-effective ways to strengthen an organization’s cybersecurity defenses. By identifying weaknesses before they are exploited, businesses can avoid costly breaches and maintain operational continuity.
- Early Detection = Early Protection: By scanning systems, networks, and applications on a regular basis, vulnerability assessments help detect security gaps before attackers do. These gaps could be anything from outdated software to weak passwords or misconfigured cloud services. Fixing them early prevents small issues from escalating into major incidents that could cause data breaches or system downtime.
- Reduces Risk of Financial and Reputational Loss: Cyberattacks can result in millions of dollars in losses, especially when customer data is compromised. A well-executed vulnerability assessment reduces this risk by proactively identifying the flaws that hackers are most likely to exploit. Organizations that stay ahead of threats are less likely to face lawsuits, fines, or loss of customer trust.
- Shortens the Exposure Window: Vulnerabilities often exist for weeks or months before being patched. Regular assessments help minimize this exposure window by continuously monitoring systems and quickly flagging any new risks. This ensures that weaknesses don’t remain undetected long enough for attackers to exploit them.
- Keeps Pace with IT Changes: The digital landscape is constantly evolving—new software, integrations, and remote work setups are added all the time. Vulnerability assessments are flexible and scalable, making them ideal for adapting to these frequent changes while still upholding strong security policies.
- Complements Penetration Testing
While penetration testing: simulates real-world attacks, vulnerability assessments provide a broader, more automated look at your system’s health. Conducting both on a recurring basis ensures you’re not only aware of existing issues, but also prepared for how they might be exploited. Together, they offer a complete picture of your security posture.
Common Approaches to Penetration Testing
Penetration testing is not a one-size-fits-all service. There are several types and approaches, each designed to simulate different threat scenarios and answer different security questions. Selecting the right type depends on your organization’s goals, risk profile, and the systems you want to test.
Also known as clear box or transparent testing, White Box testing involves full access to the target system’s internal information, such as source code, network diagrams, system architecture, and configuration files. This method simulates an attack from an internal threat actor or someone with extensive knowledge of the system.
Key Characteristics:
- Full Disclosure: Testers are granted complete access to the target environment, including source code, infrastructure details, database schemas, and configuration files.
- In-depth Analysis: Enables a thorough examination of the system’s internal logic, architecture, and code, helping identify deep-rooted vulnerabilities that external scans might miss.
- Realistic Simulation: Emulates the actions of an insider threat or advanced persistent threat (APT) with significant internal knowledge.
- Risk Evaluation: Best suited for assessing critical or high-value systems where a comprehensive security analysis is required to identify subtle weaknesses and design flaws.
White Box testing is ideal for secure development lifecycle (SDLC) processes, application security reviews, and internal infrastructure evaluations, where complete visibility is needed to minimize security risks.
Black Box testing, also referred to as closed-box testing, simulates an external attacker who has no prior knowledge of the internal workings of the system. The goal is to identify vulnerabilities using only publicly available information and external reconnaissance.
Key Characteristics:
- No Prior Knowledge: Testers begin the assessment without any credentials, source code, or network access, closely mimicking the conditions of an external attacker.
- Realistic Assessment: Provides an objective and realistic overview of what external threat actors can exploit.
- Limited Scope: Typically focuses on externally exposed services or components without delving into the internal architecture.
- Threat Simulation: Accurately models how a real-world attacker might probe and attack a system from the outside.
Black Box testing is ideal for evaluating perimeter defenses, public-facing applications, or external attack surfaces. It helps organizations understand how visible and exploitable they are from the outside.
.
Gray Box testing is a hybrid approach that combines aspects of both White Box and Black Box testing. Testers are provided with partial knowledge of the system—such as limited credentials or architectural overviews—without full access to the underlying source code or sensitive configurations.
Key Characteristics:
- Partial Knowledge: Testers work with some predefined information, allowing for targeted testing with a semi-informed perspective.
- Focused Evaluation: Balances realism and depth, enabling in-depth analysis of critical functions or workflows while maintaining a realistic attack simulation.
- Risk Reduction: Allows for vulnerability discovery without full internal exposure, maintaining a level of operational confidentiality.
- Intermediate Approach: Offers the benefits of both Black Box (realistic testing) and White Box (depth of coverage), making it ideal for many practical engagements.
Gray Box testing is useful for testing user-facing systems where some internal access can be granted (e.g., authenticated user accounts) but full source code or infrastructure details remain restricted.
Web application penetration testing simulates real-world attacks on websites, portals, and SaaS platforms to uncover vulnerabilities in the application layer. This includes improper input validation, broken authentication mechanisms, insecure session handling, misconfigured APIs, and logic flaws that could be exploited by attackers to gain unauthorized access, manipulate data, or compromise users.
The testing methodology is based on industry standards such as the OWASP Top 10, ensuring comprehensive coverage of the most critical web vulnerabilities.
The assessment includes:
- Injection Attacks: Simulating SQL injection, command injection, and other input-based attacks to identify improper validation and backend exposure.
- Cross-Site Scripting (XSS) and Cross-Site Request Forgery (CSRF) : Identifying flaws that could allow an attacker to execute malicious scripts or unauthorized actions on behalf of users.
- Authentication and Authorization Flaws: Testing login mechanisms, password reset functions, session expiration, and privilege escalation paths.
- Session Management Testing: Evaluating cookie security flags, session token predictability, and logout processes.
- Insecure APIs: Probing exposed API endpoints for lack of authentication, rate limiting, or encryption.
- Business Logic Testing: Identifying flaws in user flows, such as bypassing payment steps, applying multiple discount codes, or modifying order totals.
This type of testing is essential for e-commerce platforms, customer portals, fintech applications, and any organization with web-facing services, ensuring that both user data and application functionality remain secure under real-world attack conditions.
Mobile application penetration testing focuses on uncovering security vulnerabilities in mobile apps across Android and iOS platforms. These tests simulate real-world attack scenarios to evaluate both the app’s internal architecture and its behavior during active use. The goal is to ensure that the application is not only functionally sound, but also resilient to tampering, data leakage, and unauthorized access.
This type of testing goes beyond standard QA or functional testing—it involves ethical hacking techniques to assess how the application manages sensitive data, handles authentication, communicates with backend services, and integrates third-party components.
The assessment includes:
- Static and Dynamic Analysis: A dual-pronged approach where the app’s source code (or decompiled code) is reviewed statically, while its runtime behavior is observed during actual usage. This helps detect vulnerabilities like hardcoded secrets, insecure API usage, and improper input validation.
- Insecure Data Storage: Examining whether sensitive information—such as user credentials, access tokens, health data, or payment information—is stored locally without encryption or in areas accessible to other apps (e.g., shared preferences, external storage).
- Weak Authentication & Session Handling:
Identifying flaws such as weak password policies, lack of multi-factor authentication (MFA), token reuse, improper session timeouts, or insufficient protection against brute-force attacks. - Reverse Engineering Exposure:
Testing the app’s resistance to tools like apktool, JADX, or Hopper. The goal is to assess whether internal logic, hardcoded secrets, or API keys can be extracted and misused by attackers. - Third-party Library Risks: Evaluating the open-source libraries, SDKs, and advertising or analytics frameworks the app relies on. These components may contain known vulnerabilities or introduce privacy and compliance risks if not properly maintained.
Network penetration testing focuses on simulating real-world attacks against an organization’s internal and external network infrastructure. This includes routers, switches, firewalls, VPN gateways, wireless access points, and connected endpoints. The primary goal is to uncover weaknesses that could allow unauthorized access, data exfiltration, or lateral movement within the network.
The pen test is conducted using industry-standard frameworks such as OWASP, NIST, and MITRE ATT&CK, ensuring a systematic and effective assessment of network defenses.
The assessment includes:
- Network Enumeration: Mapping the network, identifying active IP ranges, open ports, and services running on hosts.
- Firewall and ACL Testing: Evaluating access control lists, firewall rules, and segmentation policies to detect misconfigurations and gaps.
- Protocol and Service Analysis: Identifying outdated or insecure services and protocols (e.g., SMBv1, Telnet) that may expose the environment to exploitation.
- Lateral Movement Simulation: Testing how an attacker might move across internal systems after gaining a foothold.
- Privilege Escalatio: Assessing the potential to escalate privileges and access restricted network areas.
- VPN and Remote Access Validation: Analyzing remote connectivity configurations for potential vulnerabilities.
- Logging and Detection Review: Verifying whether suspicious activities are logged and visible to SOC/SIEM systems.
Network testing is essential for any organization that relies on complex on-prem or hybrid networks and wants to proactively defend against internal and external threats.
Wireless network penetration testing targets the organization’s Wi-Fi infrastructure, aiming to identify misconfigurations, weak encryption, and potential vulnerabilities that could lead to unauthorized access or eavesdropping. These assessments simulate attacks such as rogue access points or man-in-the-middle attacks, which are common entry points for adversaries in public or semi-public environments.
The assessment includes:
- Rogue Access Point Detection: Identifying unauthorized or misconfigured wireless devices that may allow attackers onto the internal network.
- Encryption & Authentication Testing: Evaluating the security of wireless encryption protocols like WPA2, WPA3, and 802.1X, and whether user credentials are adequately protected.
- Eavesdropping Simulation: Attempting to intercept wireless traffic or extract sensitive information such as login credentials or internal communications.
- Evil Twin & SSID Spoofing: Testing how susceptible users are to connecting to fake networks that mimic trusted SSIDs.
- Guest Wi-Fi Segregation : Ensuring that guest networks are properly isolated from internal systems to prevent lateral movement.
Infrastructure penetration testing is a simulation of internal and external attacks on an organization’s IT infrastructure. The goal is to identify security weaknesses and assess the feasibility of potential intrusions across network environments, servers, and infrastructure components such as routers, switches, and communication devices.
The test is conducted according to established methodologies, including OWASP and MITRE ATT&CK, to ensure a thorough and in-depth security evaluation.
The assessment includes:
- Network Scanning – Identifying open ports, exposed services, and potentially vulnerable devices across the network.
- Communication Analysis – Evaluating whether network traffic is encrypted and protected against interception or data leakage.
- Operating Systems and Server Vulnerabilities – Identifying outdated versions, misconfigurations, and exploitable services running on infrastructure assets.
- Email Attack Vectors – Testing exposure to phishing and other social engineering tactics targeting email systems.
- DDoS Resilience – Checking for the ability to mitigate or withstand denial-of-service attacks aimed at critical infrastructure.
- Privilege Escalation – Assessing permission structures to detect misconfigurations that allow unauthorized access or lateral movement.
- Active Directory Security – Analyzing the configuration of AD environments to uncover paths to privilege escalation or compromise of the Domain Controller.
- Password Security – Evaluating password strength, reuse, exposure of password hashes, and presence of systems without authentication requirements.
IoT (Internet of Things) Penetration Testing focuses on identifying vulnerabilities in connected smart devices and their ecosystems. These devices—ranging from smart thermostats and surveillance cameras to industrial sensors and medical wearables—often operate with limited computing resources and minimal built-in security, making them attractive targets for attackers.
The testing process evaluates both the hardware and software components of the device, along with their communication protocols and backend infrastructure. It simulates realistic attack scenarios to uncover how adversaries might exploit flaws to gain unauthorized access, disrupt operations, or pivot into broader network environments.
The assessment includes:
- Firmware Reverse Engineering: Analyzing the device’s firmware to discover hardcoded credentials, insecure configurations, or undocumented features that could be leveraged by attackers.
- Device Communication Analysis: Intercepting and inspecting data transmissions (e.g., Bluetooth, Zigbee, MQTT, or Wi-Fi) to identify unencrypted traffic, weak authentication, or insecure APIs.
- Remote Access and Interface Testing: Evaluating access controls for web dashboards, mobile apps, and remote management interfaces associated with the device.
- Physical Security Checks : Assessing whether physical tampering could lead to data leakage, privilege escalation, or control override (e.g., via exposed debug ports).
- Cloud and Mobile Integration Testing: Reviewing the device’s interaction with cloud services or companion mobile apps to uncover security weaknesses in data storage, user management, or backend APIs.
Social Engineering Penetration Testing evaluates the human element of an organization’s security posture by simulating real-world deception tactics that attackers use to manipulate employees and gain unauthorized access to sensitive systems or information. Unlike technical testing, which targets software and infrastructure, social engineering tests target human behavior, awareness, and adherence to security policies.
The goal is to identify weak points in employee training, security culture, and operational procedures—before malicious actors can exploit them.
The assessment includes:
- Phishing Campaigns: Custom-designed emails that mimic legitimate communications in order to trick recipients into clicking malicious links, entering credentials, or downloading infected attachments. Success rates are measured to gauge user susceptibility.
- Vishing (Voice Phishing) : Simulated phone-based attacks where testers impersonate trusted parties (e.g., IT support, vendors) to extract sensitive information such as passwords or internal processes.
- Onsite Tailgating and Physical Intrusion: Controlled attempts to gain unauthorized physical access to restricted areas by following employees through secure entrances or using social cues to bypass security protocols.
- USB Drop Testing: Placing malicious USB drives in employee-accessible areas to test curiosity-driven plugging and data exfiltration risks.
- Awareness and Policy Assessment: Observing whether employees report suspicious activity, follow clean desk policies, or adhere to badge and access control procedures.
These tests are especially valuable for organizations seeking to:
- Improve employee cybersecurity awareness
- Detect potential insider threats or policy violations
- Validate the effectiveness of existing training programs and physical security controls
By simulating real attack techniques in a safe and controlled manner, social engineering testing helps organizations build a more resilient human firewall—an essential layer of modern cybersecurity defense.
Physical penetration testing simulates real-world attempts by adversaries to gain unauthorized physical access to sensitive or restricted areas within an organization. Ethical hackers, often referred to as “red team” operatives in this context, use social engineering, stealth tactics, and specialized tools to bypass physical security controls and test the resilience of an organization’s access protocols.
The objective is to assess how well buildings, data centers, server rooms, and employee-only zones are protected against intrusion—and to identify weaknesses that could be exploited by threat actors in scenarios like corporate espionage, insider threats, or theft of critical infrastructure.
The assessment includes:
- Access Control Bypass: Attempting to circumvent security mechanisms such as keycards, biometric scanners, PIN pads, or physical locks through techniques like lock picking, piggybacking (tailgating), or exploiting poorly enforced security procedures.
- Badge Cloning & RFID Attacks: Using radio-frequency identification (RFID) scanners or other devices to clone access cards and gain unauthorized entry. These tests determine whether current badge systems are vulnerable to cloning or skimming attacks.
- Dumpster Diving / Sensitive Document Recovery:
Examining discarded documents, hardware, or storage devices for unshredded sensitive information that could reveal internal processes, passwords, employee data, or confidential business plans. - Social Engineering Entry Attempts: Engaging with reception staff, security guards, or employees to trick them into granting access—posing as delivery personnel, IT staff, or visitors with plausible pretexts.
- Physical Device Tampering: Assessing the ability to install rogue devices (e.g., keyloggers, USB payloads, or network taps) within office areas without being noticed, to simulate how physical access can be leveraged for cyberattacks.
This type of testing is especially valuable for banks, financial institutions, data centers, law firms, healthcare facilities, or government agencies—anywhere that houses sensitive data or critical infrastructure and relies on physical barriers for protection. It’s also increasingly relevant for corporate campuses or hybrid environments where both digital and physical security are interconnected.
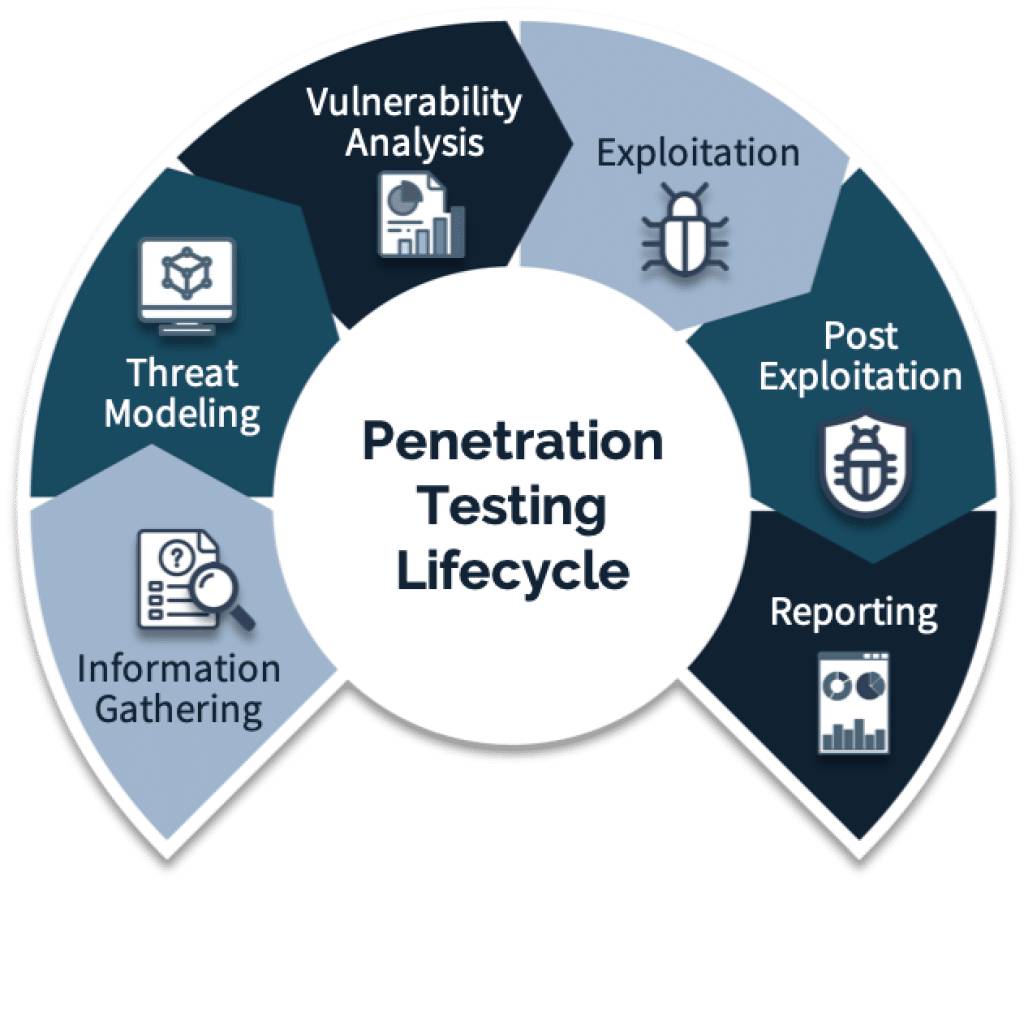
Team Methodology in Penetration Testing
A successful penetration test is not just about tools — it’s about the people, process, and methodology behind the test. At CyberSafe, penetration testing is conducted by experienced, certified professionals using a structured, transparent, and results-driven methodology. Here’s how the process typically works:
1. Scoping and Planning
The first step is understanding your business environment, goals, and risk profile. Our team defines the scope of the test — what systems will be tested, what kind of attacks are simulated, and what access level (if any) the testers will have. This phase ensures alignment with your business needs and compliance requirements.
2. Reconnaissance and Information Gathering
Our experts begin collecting public and private information about your infrastructure — just like a real attacker would. This may include DNS records, open ports, IP ranges, exposed services, and even employee data from open sources. The goal is to map the attack surface thoroughly before launching simulated attacks.
3. Vulnerability Analysis
Using both automated scanners and manual techniques, the team identifies vulnerabilities in your systems, applications, or network infrastructure. These may include outdated software, configuration errors, weak authentication, or missing patches.
4. Exploitation
Once vulnerabilities are found, we attempt to exploit them in a controlled manner to determine the real-world impact. This helps distinguish between theoretical risks and critical flaws that could be used to gain unauthorized access, escalate privileges, or exfiltrate data.
5. Post-Exploitation and Pivoting
In more advanced scenarios, our team mimics what an attacker would do after gaining access — such as moving laterally within the network, harvesting credentials, or accessing sensitive data. This step reveals how far an attacker could go and what business functions could be compromised.
6. Reporting and Recommendations
After testing, we provide a clear, actionable report with detailed findings, proof of exploitation, and prioritized remediation steps. The report is written in plain language, with both executive summaries for leadership and technical insights for IT teams.
7. Retesting and Continuous Improvement
Once fixes are implemented, a retest is performed to verify that vulnerabilities were properly resolved. This ensures that the remediation efforts were effective and closes the feedback loop between security teams and decision-makers.
What’s the Difference Between Penetration Testing and Vulnerability Assessment?
While penetration testing and vulnerability assessments are both key components of a strong cybersecurity strategy, they serve different purposes and deliver different outcomes. Understanding the distinction between them is essential for making informed security decisions.Penetration Testing: Focused on Exploitation and Real-World Risk
Penetration testing (pen testing) is a simulated cyberattack conducted by ethical hackers to actively exploit vulnerabilities in systems, applications, or networks. The goal is to mimic how a real attacker would break in, move laterally, and access sensitive information — all in a controlled, authorized manner.- Purpose: To identify actual exploitable paths into the organization and measure the real-world impact of a successful attack.
- Depth: Deep and strategic; testers often chain multiple vulnerabilities together to simulate complex attack scenarios.
- Output: A detailed report showing what was exploited, how far attackers could go, and practical remediation recommendations.
- Frequency: Periodic, often annually or after major changes to the infrastructure or application landscape.
Vulnerability Assessment: Focused on Detection and Breadth
Vulnerability assessments are automated scans and analysis processes that detect known weaknesses in systems, such as outdated software, missing patches, or weak configurations.- Purpose: To identify as many known vulnerabilities as possible across a broad range of assets.
- Depth: Wide but shallow; does not attempt to exploit vulnerabilities, only detect and classify them.
- Output: A long list of vulnerabilities, typically rated by severity (CVSS score).
- Frequency: More frequent; monthly or even weekly in some organizations as part of continuous monitoring.
So, Which One Do You Need?
Most organizations benefit from both. Here’s how they complement each other:| Scenario | Recommended Approach |
| You want to identify and exploit real-world weaknesses | Penetration Testing |
| You need a broad overview of current system flaws | Vulnerability Assessment |
| You’re preparing for an audit or compliance check | Both (start with assessment, follow with pen test) |
| You’ve just made a major change to your infrastructure | Both |
| You want to train your response teams and validate incident handling | Penetration Testing |
OUR CERTIFICATIONS








How Often Should Penetration Tests Be Performed?
Penetration testing isn’t a one-time task—it’s a critical ongoing process. As technology evolves and cyber threats become more sophisticated, organizations must continuously test their systems to stay ahead of attackers.
Recommended Frequency
Here’s when you should schedule a penetration test:
- At least once a year: Annual testing is considered the industry minimum. It helps detect newly introduced vulnerabilities and ensures ongoing compliance with standards like ISO 27001, SOC 2, or PCI DSS.
- After major changes: Launching a new web application? Migrating to the cloud? Updating your infrastructure? Each of these changes can introduce new risks—so a pen test should follow.
- Following a security breach: If you’ve suffered a cyber incident, a penetration test can help determine the root cause and uncover other exploitable weaknesses in the system.
- When required by clients or regulators: Many clients, especially in sectors like finance, healthcare, and SaaS, now demand proof of regular penetration testing as part of vendor due diligence.
- Before product or system launch: Penetration testing during the development lifecycle—especially pre-production—can prevent vulnerable code from reaching customers or users.
Why Frequency Matters?
The threat landscape changes weekly, and so does your IT environment. New users, misconfigurations, third-party integrations, or forgotten assets can all introduce exploitable vulnerabilities. Regular testing ensures that your defenses are still effective and your systems are resilient to real-world attack methods.
Organizations that test only once every few years often discover that previously secure systems have become vulnerable due to patch gaps, outdated software, or evolving attack techniques.
Pro Tip from CyberSafe
We recommend building penetration testing into your cybersecurity roadmap and aligning it with your business milestones. For example:
- Test web apps every 6–12 months
- Test infrastructure and internal networks annually
- Conduct targeted re-tests after fixing vulnerabilities
- Schedule cloud or API testing whenever new services are launched
By taking a proactive and strategic approach, you reduce the risk of unexpected breaches—and build trust with stakeholders, clients, and regulators.
How to Perform a Penetration Test?
Penetration testing is a structured and strategic process that involves multiple stages, each designed to replicate the mindset and tactics of real-world attackers. Here’s how a typical pen test is carried out:
Planning and Scoping
The first stage is all about defining the test objectives, identifying the systems to be tested, and determining the boundaries. The organization and testers agree on the type of test (e.g., white box, black box), and whether the test is internal, external, or hybrid.
Reconnaissance (Information Gathering)
Testers collect as much information as possible about the target. This can be done through open-source intelligence (OSINT), social media, domain lookups, or scanning IP addresses and subnets. In a white box setting, internal documentation might be reviewed.
Threat Modeling and Vulnerability Identification
Using tools such as Nessus, Nmap, Burp Suite, or custom scripts, testers scan for vulnerabilities in the target environment. They prioritize findings based on exploitability and potential impact.
Exploitation
Here, testers attempt to exploit the discovered vulnerabilities. This could include SQL injections, privilege escalations, or lateral movement through network shares. The goal is not just to prove the vulnerability exists, but to understand how much damage it can do.
Post-Exploitation and Lateral Movement
If access is gained, testers try to maintain persistence, pivot across systems, or extract data. This mimics how an attacker would move through the network after breaching an initial system.
Reporting
After the test is completed, a detailed report is delivered. It includes:
- A summary of vulnerabilities found
- Methods used
- Screenshots or evidence of successful exploits
- Severity levels
- Business impact
- Remediation guidance
Remediation and Retesting
CyberSafe or your internal security team applies patches, config changes, or system updates based on the report. A follow-up test ensures the fixes have been successful and no new issues were introduced.
What happens after a pen test?
Once a penetration test is complete, the real work begins. The primary goal of pen testing is not just to identify weaknesses—but to learn from them, prioritize risks, and improve your security posture.
Here’s what typically happens after a penetration test:
Detailed Report Delivery
You’ll receive a comprehensive report that includes:
- A summary of the test’s scope, methods, and findings.
- A list of discovered vulnerabilities, categorized by severity (e.g., critical, high, medium, low).
- Evidence of successful exploits (screenshots, logs, access results).
- Business impact analysis for each vulnerability.
This report serves as the foundation for the next steps in strengthening your systems.
Risk Prioritization
CyberSafe helps you understand which vulnerabilities are most urgent based on:
- Likelihood of exploitation.
- Potential business damage.
- Regulatory or compliance implications.
By focusing efforts on high-risk issues first, you reduce exposure quickly.
Remediation Guidance
The report includes actionable steps to fix each vulnerability. Our team can:
- Recommend configuration changes.
- Suggest patching or software upgrades.
- Guide code-level fixes for application flaws.
- Improve IAM (identity and access management) controls.
We can also provide hands-on support or collaborate with your internal IT/security teams.
Retesting (Optional but Recommended)
After remediation, a follow-up test—called remediation testing—is often performed to verify:
- That the fixes were implemented correctly.
- That no new vulnerabilities were introduced.
- That previously exploited paths are now fully secure.
Retesting ensures your environment is truly resilient against the attack vectors discovered.
Compliance Mapping
If your organization follows specific standards like ISO/IEC 27001, PCI-DSS, HIPAA, or GDPR, our report will help map findings to relevant controls. This makes it easier to demonstrate compliance to auditors or regulators.
Long-Term Recommendations
Beyond tactical fixes, our security experts offer strategic advice to:
- Improve your overall security architecture.
- Enhance monitoring, logging, and incident response.
- Train staff and build a more security-aware culture.
- Reduce reliance on reactive defense by implementing proactive controls.
COMMON Q&A ABOUT PENETRATION TEST
Understanding the 5 Stages of Penetration Testing
Penetration testing is a structured, step-by-step process designed to mimic real-world attacks in a controlled environment. By following a defined methodology, organizations can gain clear insights into their security posture and take informed action. Here’s a deeper look into the five core stages of penetration testing:
- Planning and Preparation
Every successful penetration test starts with clear planning. In this phase, the organization and testing team define:
- The scope of the test (which systems, networks, or applications are in-scope).
- The goals (e.g., test for data exfiltration, privilege escalation, etc.).
- The rules of engagement (how far the testers can go, what’s off-limits).
Legal and organizational approval is obtained, and all stakeholders are aligned. This ensures the test is safe, effective, and doesn’t disrupt business operations.
Example: A company wants to test only its public-facing web app, not internal servers. That boundary is set during this phase.
- Information Gathering (Reconnaissance)
The testers now act like real attackers—quietly collecting as much information as possible about the target. This can include:
- Domain names and IP addresses
- Public employee emails (for phishing)
- Open ports and exposed services
- Technology stack (e.g., Apache server, PHP version)
This phase can be passive (e.g., searching Google or Shodan) or active (e.g., scanning the network). The more data collected here, the more precise and realistic the attack simulation will be.
Example: A tester discovers that the company is using an outdated version of WordPress with known vulnerabilities.
- Enumeration and Vulnerability Analysis
Now the real digging begins. Testers enumerate systems and services—listing all active devices, users, and applications. Then, they use tools (like Nmap, Nessus, or Burp Suite) to identify vulnerabilities such as:
- Misconfigured firewalls or open ports
- Default credentials
- Unpatched software
- Weak access control mechanisms
They assess how exploitable each finding is, prioritize critical weaknesses, and plan the next move.
Example: The testers find an open FTP port that allows anonymous login—a potential entry point.
- Exploitation
This is the most high-stakes part of the test. Testers attempt to exploit the vulnerabilities found—just like a real attacker would. The objective isn’t just to “break in,” but to:
- Demonstrate how deep an attack could go
- Validate the real-world impact of a breach
- Test detection and response mechanisms (e.g., did the SOC notice the breach?)
Exploitation can involve:
- Gaining admin access to a server
- Extracting sensitive data
- Escalating user privileges
- Moving laterally between systems
Example: A tester uses a SQL injection to retrieve usernames and passwords from a database—and then uses those credentials to access internal HR files.
- Reporting and Remediation
After the test, the real value begins. Testers deliver a detailed report that includes:
- A breakdown of all findings, ranked by severity
- Screenshots and logs of successful exploits
- Step-by-step attack paths used
- Actionable recommendations for remediation
The goal isn’t to “embarrass” the IT team, but to collaborate and close the gaps. The report can also help with compliance, board reporting, and future security planning.
Example: The report may recommend disabling unused ports, enforcing MFA, or upgrading to the latest software versions. In some cases, a retest is scheduled to validate that the fixes were effective.
How Much Access is Given to Penetration Testers?
The level of access provided to penetration testers can vary depending on the type of test being conducted:
- Black Box Testing
– Testers are given no prior information about the systems, simulating an external attack scenario.
– This approach challenges the tester to discover vulnerabilities without insider knowledge, offering insights into the organization’s external defenses. - White Box Testing
– Testers receive full access to information about the systems, including source code, network diagrams, and credentials.
– This method allows for a comprehensive analysis of vulnerabilities, focusing on internal security issues. - Gray Box Testing
– Testers are provided with partial knowledge of the system, such as user-level credentials.
– This balances the insights of white box testing with the realistic simulation of black box testing.
The level of access is determined by the goals of the test and the organization’s security objectives.
Is Penetration Testing a QA?
While penetration testing shares some similarities with quality assurance (QA) processes, it serves a distinct purpose in assessing and enhancing cybersecurity posture. Unlike QA, which focuses on ensuring the functionality and reliability of software and systems, penetration testing specifically targets security vulnerabilities and evaluates the effectiveness of defensive measures.
How Does Penetration Testing Differ from Automated Testing?
While both penetration testing and automated testing aim to improve security, they differ significantly in approach and scope:
- Manual vs. Automated
– Pen testing involves human expertise, creativity, and adaptability, enabling testers to discover complex vulnerabilities that automated tools may miss.
– Automated testing relies on pre-defined scripts and tools to scan for known vulnerabilities efficiently. - Depth of Analysis
– Pen testers can simulate sophisticated attack scenarios, including chaining vulnerabilities together to achieve deeper access.
– Automated tools are limited to identifying known vulnerabilities without deeper exploitation. - Customization
– Pen testers tailor their approach based on the organization’s unique systems and infrastructure.
– Automated tools offer standardized scans without the flexibility to adapt to specific environments. - Reporting
– Pen testing reports provide detailed insights, including proof of concept for vulnerabilities, prioritized recommendations, and contextualized findings.
– Automated testing reports are often more generic and less actionable.
Pros and Cons of Penetration Testing
- Pros
1. Identifies Critical Vulnerabilities: Provides a real-world perspective on security gaps.
2. Enhances Security Posture: Helps organizations strengthen defenses against advanced threats.
3. Customizable Approach: Tailored to the organization’s specific needs and goals.
4. Compliance and Certification: Assists in meeting regulatory requirements and industry standards. - Cons:
1. Cost: Penetration testing can be expensive, especially for large or complex environments.
2. Time-Intensive: Requires significant time for thorough analysis and reporting.
3. Temporary Insight: Provides a snapshot of security at a single point in time; regular testing is required to maintain effectiveness.
4. Potential Disruption: If not carefully planned, testing can inadvertently impact systems or services.
How Penetration Tests Are Conducted
Penetration tests are carried out using advanced tools that simulate a wide range of attack scenarios, with the goal of identifying security vulnerabilities at various levels. The assessments focus on detecting gaps such as missing security patches, unsecured access permissions, vulnerable IoT devices, and more.
In addition, targeted manual attacks are performed using advanced techniques and tools. This process simulates realistic attack scenarios to identify and exploit vulnerabilities in communication layers, internal and external networks, operating systems, databases, and communication components.
The objective is to assess the potential for unauthorized access to organizational resources and to provide actionable recommendations for hardening and improving the overall security posture.
Will penetration testing impact business operations?
When planned carefully, penetration testing should not disrupt normal operations. The scope and methods are designed to minimize risks.
What qualifications should a penetration tester have?
Penetration testers should have certifications such as CEH (Certified Ethical Hacker), OSCP (Offensive Security Certified Professional), or CISSP (Certified Information Systems Security Professional), alongside practical experience.
Can penetration testing guarantee complete security?
No, penetration testing identifies vulnerabilities and improves security but cannot guarantee complete protection against all threats.
How is Penetration Testing Done?
Penetration testing is not a one-size-fits-all activity. It’s a structured, hands-on process that blends human expertise with automation to simulate real-world attacks. The goal is to discover security weaknesses before malicious actors do. Here’s how the process typically works:
1. Manual Testing
While automated tools are helpful, many vulnerabilities require a human touch to uncover. Skilled penetration testers use creative thinking, pattern recognition, and deep technical knowledge to:
- Chain together multiple low-severity issues into a critical exploit
- Identify logic flaws, insecure workflows, or access control failures
- Mimic the behavior of real-world attackers (including social engineering or insider threats)
Example: A tester notices that a password reset process lacks verification and uses that to take over a user account.
2. Automated Tools
Automation plays a key role in speeding up and scaling the process. Tools can quickly scan for known vulnerabilities, open ports, and misconfigurations. Common tools include:
- Nmap – for network scanning and host discovery
- Nessus – for vulnerability assessment and risk ranking
- Burp Suite – for web application testing and injection attacks
- Metasploit – for exploit development and payload delivery
These tools help testers cover a wide surface area efficiently while still allowing manual exploration of critical issues.
Note: Automated tools alone are not enough—they may miss business logic issues, chained exploits, or zero-day threats.
3. Custom Scripts and Payloads
In some cases, off-the-shelf tools aren’t sufficient. Testers may write custom scripts or payloads to simulate advanced attacks or bypass layered defenses. This is especially common in:
- Mobile app testing (e.g., creating custom API fuzzers)
- IoT testing (e.g., reverse engineering firmware)
- Cloud testing (e.g., privilege escalation in IAM roles)
4. Continuous Iteration and Analysis
Penetration testing is an iterative process. Testers learn more about the target as they go, adapting their tactics along the way. For example:
- A low-level vulnerability found early on may later be used for full system compromise.
- A small misconfiguration may lead to lateral movement across the network.
This approach mirrors the adaptive nature of real-world attackers.
5. Collaboration and Reporting
Throughout the test, penetration testers may work closely with internal teams—especially in gray-box scenarios. After completing testing, they deliver a comprehensive report with:
- Proof-of-concept screenshots or logs
- Technical root causes of each vulnerability
- Clear, prioritized recommendations for fixing each issue
Exploring Tools Used for Penetration Testing
Effective penetration testing relies not only on skilled professionals but also on a suite of powerful tools that help uncover vulnerabilities efficiently and accurately. These tools support different phases of the test—from reconnaissance to exploitation—and help simulate real-world attack scenarios. Below are some of the most widely used tools in the field:
Nmap (Network Mapper)
Purpose: Network scanning and host discovery
Nmap is a staple tool in any penetration tester’s arsenal. It’s used to:
- Identify live hosts on a network
- Detect open ports and running services
- Map firewall rules or access control lists
- Perform basic vulnerability scans via scripts
Use Case Example: Scanning a corporate network to find outdated services that could be exploited.
Metasploit Framework
Purpose: Exploitation and payload delivery
Metasploit is an open-source framework designed to develop and execute real exploits against systems. It allows penetration testers to:
- Simulate attacks using a vast library of known exploits
- Test system defenses in controlled environments
- Validate the severity of identified vulnerabilities
Noteworthy Feature: It can also be used for post-exploitation (e.g., privilege escalation or pivoting within a network).
Burp Suite
Purpose: Web application security testing
Burp Suite is one of the most widely used tools for assessing web-based applications. Its core features include:
- Intercepting proxy to inspect and modify HTTP/S traffic
- Automated vulnerability scanning (e.g., XSS, SQLi)
- Intruder tool for brute-force and fuzzing attacks
- Repeater and Sequencer for testing session handling
Ideal For: Testing login forms, input validation, and complex application workflows.
Wireshark
Purpose: Network traffic analysis
Wireshark is a protocol analyzer that captures packets in real time, allowing testers to:
- Analyze traffic for sensitive data (e.g., passwords in plaintext)
- Detect anomalies or malicious communication patterns
- Troubleshoot network issues or replay traffic
Use Case: Identifying whether credentials or session tokens are transmitted over unencrypted channels.
Additional Tools Commonly Used
- Nessus – A vulnerability scanner that identifies known security issues across systems.
- Hydra / Medusa – Tools for brute-force password attacks across multiple protocols (SSH, FTP, RDP, etc.).
- SQLMap – An automated tool to detect and exploit SQL injection vulnerabilities.
- John the Ripper – A fast password cracker used for testing password strength.
- Aircrack-ng – A suite of tools for auditing wireless networks, including cracking WEP/WPA keys.
- Nikto – A web server scanner for outdated software, misconfigurations, or default credentials.
- Amass – A tool for advanced asset discovery, subdomain enumeration, and DNS reconnaissance.
- BloodHound – Visualizes and analyzes Active Directory permissions and relationships to identify attack paths.
The 8 Stages of Penetration Testing Revisited
Penetration testing can also be categorized into eight stages:
- Reconnaissance:
– Define objectives, scope, and rules of engagement.
– Collect information about the target, such as IP addresses, domains, and technologies. - Scanning:
– Use tools to identify open ports, services, and potential vulnerabilities.
– Assess how the target systems respond to various intrusion attempts. - Enumeration:– Build upon the results of scanning to gather detailed system data.– Focus on discovering and cataloging assets, users, and services that could be exploited
- Vulnerability Analysis:
Vulnerability Analysis is a pivotal stage where the information gathered from scanning and enumeration is meticulously analyzed to identify exploitable weaknesses. This step involves:
– Mapping known vulnerabilities
– Identifying application-specific issues
– Validating exploitabilityTools like Nessus, OpenVAS, and Qualys are commonly used, but manual analysis is crucial for uncovering complex vulnerabilities that automated tools may overlook. This phase ensures a clear understanding of the risks and helps prioritize mitigation efforts effectively.
- Exploitation:
– Simulate attacks to exploit identified vulnerabilities.
– Demonstrate the potential impact of successful exploitation, such as data theft or system compromise. - Post-Exploitation:
– Assess how far an attacker could penetrate the system and the level of access they could achieve.
– Evaluate the ability to maintain persistence within the environment. - Reporting:
– Document findings, including exploited vulnerabilities, their impact, and recommendations for remediation.
– Prioritize vulnerabilities based on risk and potential impact. - Remediation Verification:
– Conduct follow-up testing to ensure vulnerabilities have been effectively addressed.
– Confirm that implemented security measures mitigate identified risks.
IS YOUR BUSINESS REALLY NEED A PENETRATION TEST?
There is another type of technical security testing which often tends to be confused with penetration testing namely : “Vulnerability assessments.”
Yet they couldn’t be more different, the financial costs the information obtained and the effort that required.
You should make sure which one you need, if you’re uncertain about your assessment needs, contact us!
GET CYBERSAFE EXPERTS ON YOUR SIDE
CyberSafe Security is a leader in Penetration Testing and Vulnerability Assessment.
We’ve been providing advanced security testing services since 2003; testing hundreds of companies
to validate and confirm that their business-critical objectives and information are safe.
As an industry leader, we are committed to maintaining the highest levels of training and certifications for all our security testing experts
. Our penetration tests use both automated tools developed in-house, as well as well-known industry tools.

